Gain Complete Visibility of Your Cybersecurity Assets with the SJULTRA CAASM free trial.
Get a comprehensive view of your IT/OT and cybersecurity assets within 30 days. We work with you to quickly set up Axonius, then hand-craft your custom cybersecurity asset attack surface management report covering gaps and remediation.
How the SJULTRA Free Trial works.
Actions
- Contact us via any of our channels.
- Quick kickoff meeting to explain the process
- We integrate the Axonius solution (non-disruptive)
- Data collection begins immediately
- Receive a detailed presentation and comprehensive report on findings
- Get our expert remediation recommendations
No obligation to continue, no subscription, no lock-in. Keep your data and report even if you decide not to move forward.
Outcomes
- Comprehensive Asset Inventory: A complete overview of all your IT and OT assets
- What’s Good: Highlight strengths and well-managed areas
- What’s Bad: Vulnerabilities and risks
- Gaps: Uncovering blind spots in your current asset management approach
- Expert Recommendations: Actionable steps for remediation and improvement
- Presentation: A walkthrough of the findings and recommendations by our cybersecurity experts
What SJULTRA customers say
Frequently Asked Questions
Can I self-serve?
You can go direct to Axonius and learn from scratch, or you can get their faster and leverage our experience.
What’s the catch?
No catch. No cost. No obligation.
How long does it take?
We kick off within a week of hearing from you.
Any limitations?
We limit the amount of integrations and assets in the trial.
8 Compelling Events that drive CAASM projects
Complex IT/OT
Our CMDB was inaccurate and out of date, because our IT/OT changes all the time and our tools are like silos of data. There’s no single source of truth we can trust.
skills and tools
Our team turnover has left us with missing skills and less bandwidth, so these important cybersecurity jobs aren’t getting done.
Red Team Audit
The Red Team found unpatched devices, and this solution found out why: they weren’t being patch managed.
M&A
We bought several companies and there was no way to “see” across them all, which is what we needed to merge them.
MSP Offboarding
Prepare for MSP people and process handover by using CAASMCyber Asset Attack Surface Management (CAASM) focuses on man… to analyze all systems and their integrations, answering important queries.
Technology Migration
Migrating on/off the cloud or off-boarding VMware are common compelling events where CAASMCyber Asset Attack Surface Management (CAASM) focuses on man… provides full sight.
New Leadership
As a new CIO, my 90-day plan includes surveying the IT landscape: and if I can’t do that, then there’s an immediate problem.
Compliance Failure
We can’t prove to the auditor that we are following our own security policies. This solution codifies our policy into practice.
Outcomes from the SJULTRA CAASM Solution
Features
- Automated inventory and discovery of assets
- Continuous monitoring and reporting of asset data
- 1,000 security and IT management integrations
- Customizable dashboards and reports
- Remediation workflow automation
- Policy enforcement and compliance monitoring
- User behavior and risk analysis
Benefits
- Enhanced cybersecurity posture
- Increased operational efficiency
- Reduced risk and exposure to threats
- Compliance with industry and regulatory standards
- Cost savings through automation and streamlining of processes
- Streamlined communication between IT and security teams
- Quick and easy deployment
Top 3 objections to starting a CAASM project
We have Existing cybersecurity tools
Who needs more tools? Axonius is different in that it aggregates *everything*, which can lead to removing other tools to save money. No other tool does what Axonius does.
CAASM isn't a priority Right Now
Cybersecurity asset management isn’t exciting…until it is. Security breaches, failed audits, and wasted spend is the kind of excitement you can do without.
We don't have this problem at all
CMDB uptodate and accurate? Got multiple MDRs? XDRs? Patch Management? Vulnerability Analysis? Do they all tally and say the same thing — or do you have unknown unknowns?
Get your Axonius 30-day Trial from SJULTRA
- Dashboard showing unique device and user counts
- Adapter configuration process
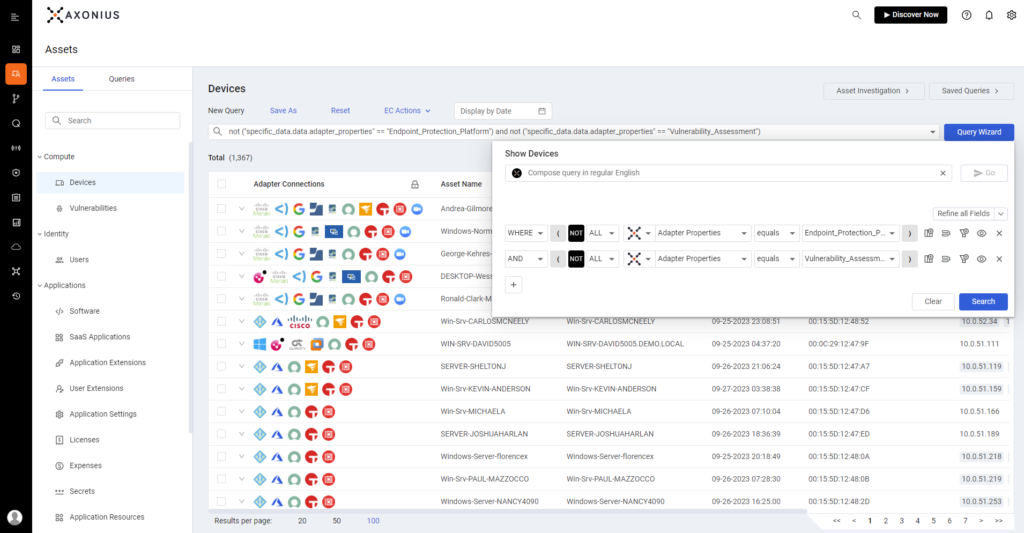
- Detailed view of individual devices, including aggregated data from multiple sources
- Query wizard for creating complex searches (e.g., Windows devices without McAfee, public cloud assets not scanned for vulnerabilities)
- User permission and configuration queries
- Cloud asset compliance add-on (e.g., CIS benchmarks for various cloud providers)
- Automation of actions based on policy violations
- Various response options: notifications, ticket creation, scheduled scans, user management in Active Directory
- Over 115 pre-built actions available
- Any query can be turned into a dashboard chart for easy visualization and tracking over time
Watch an Axonius demo
Why Axonius?
Asset management in cybersecurity is difficult due to siloed solutions with conflicting or incomplete data.
It’s challenging to answer questions about security agent installation, unmanaged devices, and cloud instance configurations.
Axonious is an aggregator, collecting and correlating information from various security and IT solutions.
What does Axonius do?
Comprehensive asset inventory (devices, users, cloud assets, SaaS applications)
Identification of coverage gaps and policy deviations
Automated policy validation and action triggers
Implementation
Deployed as a virtual appliance or SaaS solution in hours
Agentless, non-disruptive and doesn’t require network scans. Ideal for sensitive OT networks.
1,000 adapters to integrate to most assets and systems.